Malware
This is one of the parts of Cybersecurity almost everyone has had some form of experience with. You may have gotten a more generic virus once, or perhaps a worm, or maybe you were hit with ransomware. There seems to be never ending types of malware out there. In this post, we're going to talk about the many types of malware, what they are and how they function.
Before we talk about the specific types of malware, we'll look at what malware even means. Malware is a blended word, combining the words Malicious and Software. You'll often hear people use the word virus as a catch-all for any type of malware, but this is incorrect as you'll see why very shortly. Malware ranges from intentionally destructive like ransomware, to stealthy like rootkits. This isn't a history lesson on malware, so I won't be talking about the first malware (called The Creeper, of which the podcast Malicious Life has an excellent episode about called The Ghost in the Machine).
Virus
A virus is one of the most common types of malware out there. Viruses work by attaching themselves to legitimate files and spread themselves by infecting other files. They have a variety of goals, as well as a variety of subtypes that make up viruses. I'm only going to talk about four, but there are more than this. I don't want to make this blog post bigger than I feel like it already will be.
Bootsector Virus
A bootsector virus is a sub-type of the virus family of malware. This type of virus targets the Master Boot Record (MBR) of comptuers and infects them at the BIOS level. This enables an insane level of persistence, as it can reinfect devices even if the entire operating system is reloaded. The only way to remove a bootsector virus is to re-flash the BIOS. For a long time, UEFI was not affected by bootsector viruses, but there have been some discovered recently, such as MoonBounce.
Polymorphic Virus
Polymorphic viruses mutate their code to enable it to hide from signature-based antimalware systems. The virus will keep the same basic routines each time it infects a device, but multiple aspects of the malware's code will change each time to enable that detection avoidance capability. Several examples exist of polymorphic malware, including URSNIF, VIRLOCK, and BAGLE.
Macro Virus
A macro virus is a type of malware that targets the macro languages of certain types of applications. Most commonly, you'll see macro viruses for Microsoft Excel and Microsoft Word. This makes it OS-agnostic (to a point). Since both macOS and Windows can run Microsoft Word/Excel, they can both be infected by Macro viruses. The best example of a maro virus is the Melissa virus.
Worm
A worm is a very common type of malware, although it's often used as a transmission medium to other types of malware now. Worms exploit vulnerabilities in a variety of operating system to make copies of themselves throughout networks and connected endpoints. These may be vulnerabilities that let them travel through networks, or exploits using flash drives.
When we look at Worms, there have been some big names in the past. ILOVEYOU of 2000, Conficker of 2008, and Stuxnet of 2010 (while technically a worm, it could also have been considered a "Cyber Weapon". Malicious.life has a great 3 part podcast [Part 1, Part 2, Part 3] on Stuxnet). We've seen more modern worm attacks in the Russo-Ukraine war of 2022, as part of the HermeticWiper attacks. The worm component is known as HermeticWizard.
Ransomware
Ransomware is the big name malware right now. Almost every piece of news you read about a compromised company talks about the use of ransomware. Just a few days ago, Chicago Public Schools sent out a notice that the personal information of students was breached during a ransomware attack. In 2020, various parts of the Baltimore, MD government were hit with a ransomware attack. We've even seen a few police departments hit with ransomware. Would I even be a Cybersecurity professional if I didn't mention that at least a large part of the Costa Rican government's systems were recently hit with ransomware as well?
So why has there been such a huge uptick in ransomware? It's the most likely to be profitable. We're seeing multiple styles of ransomware. Encrypting ransomware, where the data is encrypted in a way that makes it theoretically impossible for the victim to access their data without paying the ransom to get the decryptor key. We're also seeing ransomware used in a double ransom scenario. Where the victim is ransomed to gain their decryptor key, and has a separate ransom to keep their data from being leaked.
While most "reputable" ransomware gangs will give the decryption key back, it's always questionable if they will give it back. However, during the Russo-Ukraine war, we've seen ransomware whose only goal is destruction, with no way to get the data back. Ransomware has also lost some profitability during the Russo-Ukraine war, and is rumored to be behind the recent disbanding of the Conti ransomware group.
Throughout the years, we've seen many different ransomware strains. From WannaCry to NotPetya, BlackMatter to Locky. This is only four of the many strains of ransomware, and it will only ever be many new ones in the future. If you want to see some great detail on Ransomware, Blackberry just posted an excellent article on the Chaos and Yashma Ransomware.
Adware
Adware has mostly fallen out of style, but it is far from dead. Adware is a type of malware whose primary goal is to cause a ton of popup ads to show up on your computer. These were one of the big culprits behind the kind of malware that would show tons of pornographic ads on computers many years back. Adware has mostly fallen out of style because it is far less profitable than Ransomware or even cryptominers. The bet example I can give of Adware is Fireball.
Spyware
Spyware is/was often confused with Adware, with many not understanding the real difference. While adware focused on displaying ads on your device, Spyware focused on collecting information about a user. Think passwords, PINs, payment information and other such information. DarkHotel is an excellent example of Spyware.
Keyloggers
Keyloggers are a subtype of Spyware that monitor user activity. Keyloggers have both legitimate uses and malicious purposes. When used in a legitimate manner, you'll see businesses using them to monitor an employee's activity or for parents to track children's online behaviors. I'm not advocating for this use, by the way. I think either one is a huge invasion of privacy and shows a lack of trust for your employees (or children).
However, they are often used in a malicious manner, being used to steal sensitive information like passwords or banking information. One of the more popular keyloggers is Olympic Vision.
Scareware
Scareware is less common than it used to be, but it is one of those types of malware that will never truly be gone. Scareware is simple: It doesn't do much of anything except attempt to scare you into paying the attacker some form of crypto or other payment. There are multiple types of scareware, but they all have the same underlying technique: Scare you to get you to pay them.
One of the major types was the fake antimalware software. You'd install this antimalware and it would "detect" a ton of malware "for free" on your device. However, to remove them, you'd need to pay the scareware author. This would unlock a key that would "remove" all of the "malware". The FBI posted an example of this type of scareware back in 2011.
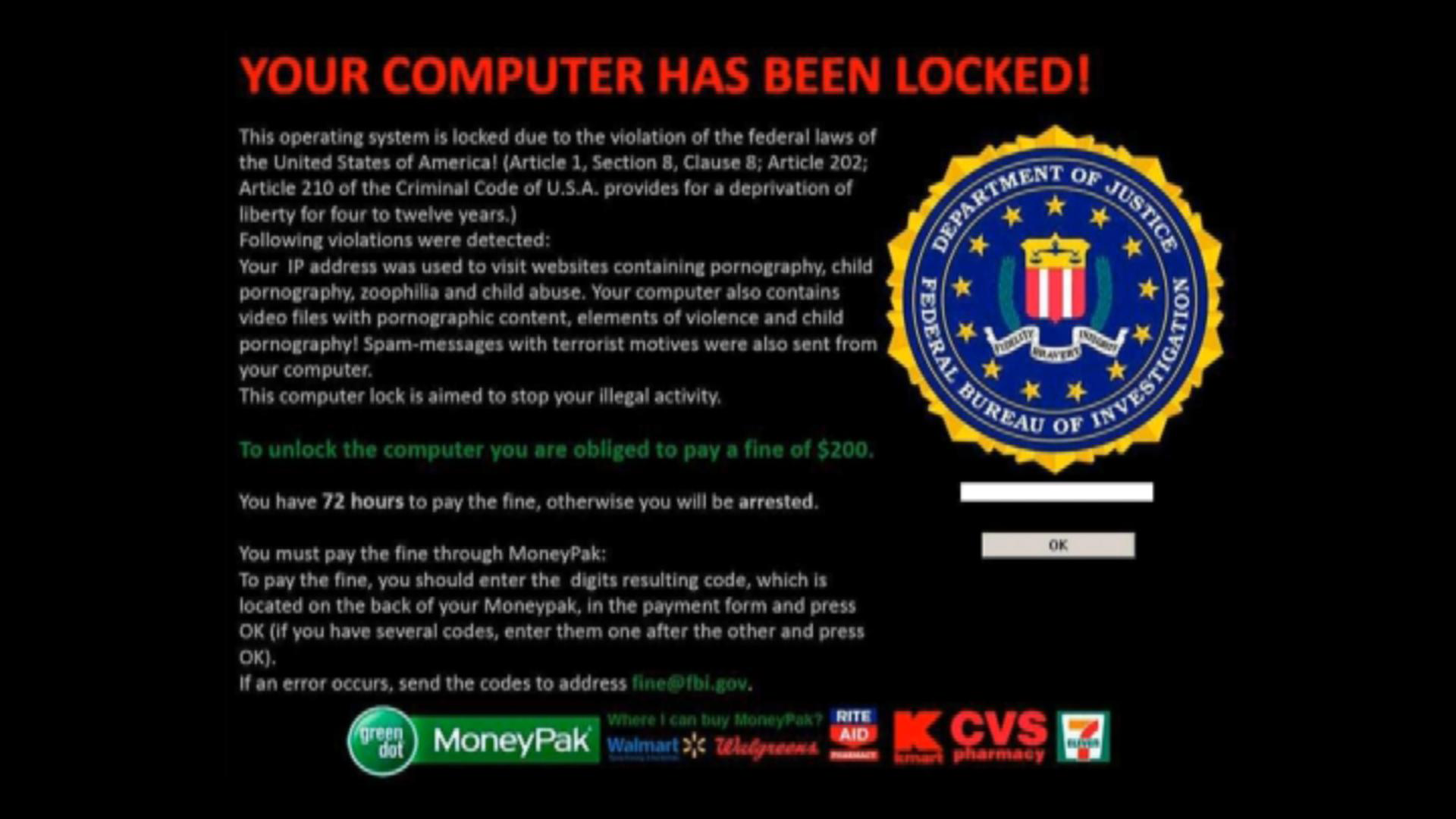
The other common type was the FBI scareware, where you were told your computer was locked due to illegal activities on your computer. You were of course told that you can unlock your computer by paying the fine. This makes absolute sense, especially paying the FBI through MoneyPak, but that's another story.
Fileless Malware
Fileless malware is a bit of a unique method for malware. Most of types of malware drop some type of file on the computer and execute it. This is generally an executable (.exe) file, although it may be a .vbs or .bat file as well in certain circumstances. However, fileless malware doesn't install anything, at least at first. It generally executes by taking advantage of native operating system features, such as PowerShell or Windows Management Instrumentation (WMI).
Many fileless attacks are undetectible by the more traditional endpoint security products, like traditional antivirus, whitelisting, and other techniques. They are detectable using Endpoint Detection and Response (EDR) or eXtended Detection and Response (XDR) systems, however. There are a few examples of this type of malware I'll give. Just based on the name, one of my favorite examples is Frodo, but another example is Astaroth.
Trojans
Trojans take the act of hiding in software to another level. Trojans will disguise themselves as desirable software, often hiding in games, apps and software patches. Trojans will then be used to execute malicious activities on the device or download additional malware. Trojans are also often called Remote Access Trojans, or RATs. Emotet is the best modern example of a Trojan.
Trojans are often confused for a virus, and it's easy to see why. They both hide themselves in legitimate code and use that as their entry point into a computer. However, viruses can only run when the legitimate software is ran, while Trojans can run outside of it. I also want to point out that it is rare that malware fits into a single one of these categories easily. For example, earlier I categorized Stuxnet as a worm, but more accurately, it is not only a worm, but a virus and a rootkit as well.
Bots
Bots are small applications that threat actors use to execute remote commands on a system. When used in a malicious manner, they are most often used to launch Distributed Denial of Service (DDoS) attacks. When multiple computers which have bots installed are counted together, this is called a botnet. One of the most well-known botnets is the Mirai botnet, which infected anywhere from 800,000 to 2.5 million computers.
Cryptominer (a.k.a., Cryptojacking)
It's rather easy to guess what cryptominers do. They use your computer (along with a massive amount of other infected computers) to mine for some form of crypto. Bitcoin, Monero, Ethereum, the list goes on. There are many ways for a cryptominer to function. There is of course installed cryptominers, like BadShell (a very short summary on BadShell is found at CSOOnline. Note that BadShell is also a form of Fileless malware!). There are also browser based (or Javascript) cryptominers. One very good example of this form of cryptojacking is Coinhive. Browser-based cryptominers are far less efficient than installed cryptominers, but browser-based ones can temporarily infect (as it is only active while a user is on the site) far more users when put on a popular site, than an installed cryptominer will.
Conclusion
I hope you enjoyed this article, and I look forward to writing the next one! As always, if you have any particular Cybersecurity topics that interest you, please don't hesitate to reach out to me using any method on my Contact page and let me know!

