It's been about almost a month since my last post, and I apologize for that. Work has been incredibly busy, and then I was sick for almost a week with what was basically a long version of the 24-hour stomach bug. It's been crazy. However, I'm coming back swinging and hope this blog post is of interest!
I made a short post on LinkedIn today about Threat Modeling and how important it is. Feel free to read it here, but I'll be repeating (and expanding) upon most of it in this post.
Threat modeling is, in my opinion, an essential task in Cybersecurity and yet it so underappreciated. There are many security professionals out there who do not know how to do threat modeling, or if they do it's at a very cursory level. Part of this is because many companies still see Cybersecurity as a compliance related task, but that's changing.
Threat Modeling is a way of breaking down your application, network, or other IT system and finding potential attacks against that system. This goes hand in hand with risk assessment (although PASTA includes risk assessment as part of it), because after you find these potential attacks, you need to determine the risk is presents to an organization, so we'll talk about both in this post. I'll be talking about 2 threat modeling techniques (although many exist), at short about STRIDE and at length about PASTA. I'll then provide a short overview about three risk assessment methodologies, which are DREAD, NIST SP 800-30, and FAIR, and link to a good video for each of them.
STRIDE
STRIDE is one of the original threat modeling techniques that has been around for a very long time. STRIDE stands for Spoofing, Tampering, Repudation, Information Disclosure, Denial of Service, Elevation of Privilege. It looks more statically at threats, but it is easy to use and can get some quick results. As Tony UcedaVélez says in the video I link later, it's not perfect anymore.
This is a good video on STRIDE.
PASTA
PASTA, or the Process for Attack Simulation and Threat Analysis is a risk-centric approach to threat modeling. From the very beginning, you are looking at the risk in regards to the organization's business objectives. PASTA follows several stages for threat modeling. I want to note that a lot of what I discuss below is revolved around an excellent video by Tony UcedaVélez, the co-writer of the PASTA methodology, which I link to at the end of this section. This post is high level, so watch the video.
Stage 1: Define Objectives
You need to determine the risk, or even moreso, what is actually important to the organization in terms of their business objectives. Commonly, these objectives map to one of several areas: External Frameworks like CoBIT, NIST, or CIS; Internal Standards like Crypto, Authentication, and .NET Security; External Regulations like PCI-DSS, NERC CIP, or FedRAMP; and Internal Processes/Artifacts like Risk Assessments and Vulnerability Assessments. Once you understand these objectives, you can map the business objectives to security requirements.
Stage 2: Define Technical Scope
You start this by defining the attack surface for the system. Things like the API endpoints, Network Infrastructure, DNS Server, or Data Storage Device. The goal is to determine what exists in related to the system, as any of these can result in a potential method of attack against the system you are modeling for.
Stage 3: Application Decomposition
Here we determine how the application actually works. We look at trust boundaries, data flow (and how they flow across trust boundaries), who is calling for certain flows, and the components we discovered in Stage 2 relate. This is documented in a Data Flow Diagram, or DFD. This is one of the main outputs of Stage 3. DFDs can be made in OWASP Threat Dragon and Microsoft Threat Modeling Tool (which also can do some automated STRIDE analysis).
Stage 4: Threat Analysis
In this stage, we do a good portion of our analysis. The best way to do this is to bring in threat intelligence. Understanding what attack behavior targets your industry can help you understand what types of attacks may target your system. Some great sources are Cyware's newsletters (Monthly, Daily), an Information Sharing and Analysis Center (ISAC) for your industry, MISP, and many others. And of course, take a look at what is actually happening in your environment (logs!).
Stage 5: Vulnerability and Weaknesses Analysis
Take a look at the vulnerabilities within the application that support the goals of the threat. For example, an attack wants to gain access to confidential data about your company in order to gain a competitive edge in the market. Stealing client information, IP information, products in development, or other things.
You need to look at the design of the application, the code, the layout of the network, existing security measures and how they may not be effective, and other analysis techniques to find potential vulnerabilities. This could also be assisted by vulnerability scanners like Tenable or Rapid7 to a point, but it only helps with portions.
Stage 6: Attack Modeling
This is where you actually model the attacks that might happen against your system. Each parent node should be the threat objective, and each underlying node from that should be the target. All subsequent layers are pulled from attack libraries. There's an example in the video on what this looks like, but I screenshotted it and pasted it right below.
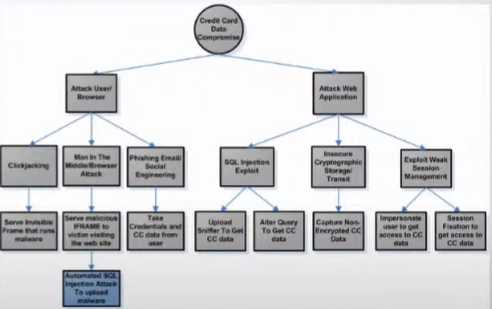
Remember that the goal of PASTA is to think like an attacker as you go through it. These attack trees are blueprints for an attack. That's why the top (parent) node is what the threat objective is, while the lower layers are sort of a "how to" for the attack.
Stage 7: Risk & Impact Analysis
This maps back to the residual risk formula. That is, RR = (((Vulnerability * Probability of Vulnerability) * (Threat * Probability of Threat)) * Impact)/Countermeasures (as shown in Tony's video, RR=[(tp * vp) * i]/c. As you can see, this is different than the more traditional Risk formula, which is Risk = Threat * Vulnerability * Impact.
There is no one better to give you a great look at PASTA than Tony UcedaVélez, who co-wrote the PASTA methodology with Marco Morana. You can watch his video on PASTA below. You can also purchase his book on the PASTA methodology on Amazon.
DREAD
DREAD stands for Damage, Reproducibility, Exploitability, Affected Users, and Discoverability. These map roughly to: Damage - how bad would an attack be? Reproducability - How easy is it to reproduce the attack? Exploitability - how much work is it to launch the attack? Affected users - how many people will be impacted? Discoverability - how easy is it to discover the threat?
The last D, Discoverability, causes debate. Just because a vulnerability is not easily discoverable does not mean it should be rated lower. That's the common argument. So some advocate removing the Discoverability element altogether, or just setting it to it's max value. Which also can vary.
Some advocate for using DREAD on a 0-10 model, while some do a 0-3 model. In other words, 0=None, 1 = Low, 2 = Medium, 3 = High. Or 0 = None, 10=Critical (and a range between). Some say you then take the total and divide by 5, some just have a scale that goes up to the max with certain numbers being high (for example, 12-15 = high if you use the 0-3 model).
Regardless of these inconsistencies, DREAD is a good qualitative model to use. I don't have one good, longer video to discuss DREAD, so I'll link three shorter ones below.
Dr. Auger talks about DREAD in passing, but this is a great video
NIST SP 800-30
This is sort of the granddaddy of risk assessment methodologies. 800-30 is thoroughly documented on NIST's website and is currently at revision 1. The PDF is available here. I'll let their documents and the below video speak for how NIST SP 800-30 is used for risk assessment.
FAIR
FAIR, or Factor Analysis of Information Risk, is another great risk assessment methodology. I also can't add anything beyond what the video below does, and would rather redirect you to the video to learn more about FAIR.
Conclusion
If you take the time to learn how to do Threat Modeling, and do it well, you'll set yourself apart from many of the other security professionals out there. PASTA is probably one of my favorite threat modeling methodologies, but it's not the only one. Take the time to read about multiple threat methodologies (this whitepaper covers the most popular), and become very familiar with a few. But do yourself a favor, and make PASTA one of the ones you become very familiar with.